
Developing A Plan for Data Protection
Data breaches have become so common that they are no longer news. Gartner predicts, “as more companies look to benefit from data, there will be an inevitable increase in data use and sharing missteps.”

Get Your Business Ready for the Cloud with a Strong Strategy
While many businesses have already adopted cloud computing to a certain extent, others are still new to the technology. Whether your business is using cloud computing already, or is considering a move, it’s never too soon to develop a strong strategy. Read on to learn more about developing a strategy to guide your business in considering cloud computing.

Network Monitoring for Your Business
Your organization’s computer network is the backbone of your IT operations, supporting data and applications such as Voice-Over IP (VoIP), call center and more. Monitoring this network can help save time and money. Read on to learn more about the benefits of network monitoring, and what to consider before adopting a solution.

What is Infrastructure as a Service (IaaS)?
Cloud computing is now a common way for small to medium-size businesses to provision computing resources for flexible, cost-effective results. Read on to learn about how one cloud model–Infrastructure as a Service or IaaS–can help your business manage spend and maximize results.

Business Continuity in Challenging Times
It is never too soon to consider what your business will do in the event of a disaster–a cyber attack, a natural disaster, or an epidemic. In the Covid-19 pandemic and subsequent quarantine, many businesses have still managed to continue operating with employees working from home.
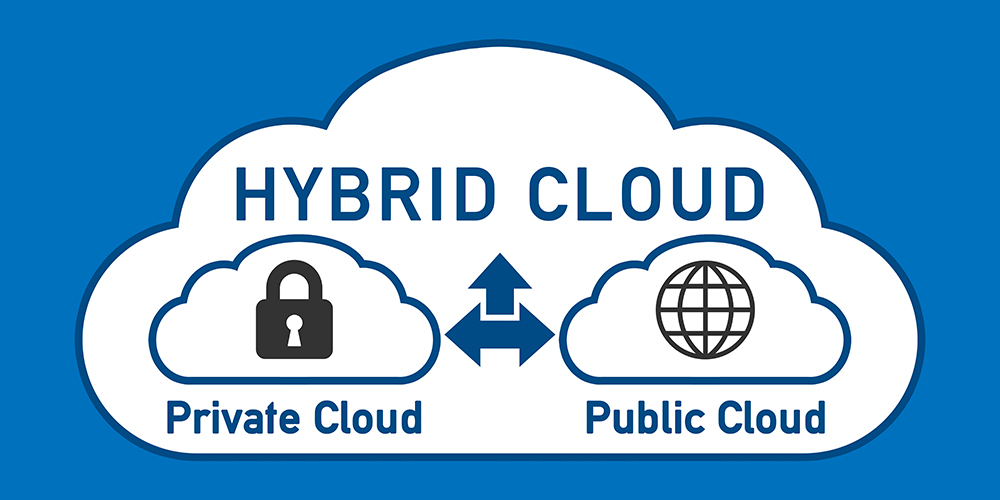
Choosing the Best Cloud Environment for Your Business
Cloud computing, once an emerging technology, is now common, and is proving valuable in this time of remote work resulting from the COVID-19 quarantine. To access data and applications, all that is needed is a computer and an Internet connection.

Keeping Your Network Secure in the Era of Remote Work
Approximately two months have passed since the beginning of social distancing, and working from home has become the norm. Virtual private networks are a way for remote workers to access the business’ system from home and therefore keep working, and these networks need to stay strong and secure.

Cybersecurity in Challenging Times
In these unprecedented times, we spend more time than ever on various devices, using them both for work and recreation. As in other difficult times, heroes rise to the occasion. However, so do bad actors, seeking to take advantage of the situation. Read on to learn more about protecting yourself from cyber attacks.

Requirements for Remote Office
With remote workers becoming the ‘new normal’ in these strange times, remote office security and communication become increasingly important. Read on to learn more about preparing your employees and business for remote work.
Helping You and Your Business Survive and Thrive During COVID-19
In the last month off dealing with COVID-19, many workplaces have shut down their offices. Many employees are working remotely, and meeting via web-conferencing platforms. Read on to learn more about keeping safe, healthy and productive during unusual times.
